CryptoLocker Ransomware and the Importance of a True Enterprise Backup
 Virus and malware infections have been increasing throughout this year, with our techs having seen the most infected machines ever in the last few months. We’re no longer talking about malicious items in the hundreds, we’re now seeing numbers in the thousands on a single computer.
Virus and malware infections have been increasing throughout this year, with our techs having seen the most infected machines ever in the last few months. We’re no longer talking about malicious items in the hundreds, we’re now seeing numbers in the thousands on a single computer.
Just when many people are being overwhelmed with the amount of viruses and malware on the Internet in September a new ransomware called Cryptolocker was discovered.
Ransomware’s first known appearance was in 1989, called the PC Cyborg, it required people to pay $189 to “PC Cyborg Corporation” in order to unlock the infected system. Ransomware works in several ways, first entering the system typically through a downloaded file or network vulnerability, from there it either begins to encrypt files or restricts interaction with the system in a variety of ways. Ransomware’s goal is to extort money from the system’s user in order to make their computer operational again. After payment the victim is either provide the decryption key, unlock code or is occasionally left hanging having paid the money, but not provided anyway to access their files.
The newly discovered Ransomware, named Cryptolocker, is delivered to the system as an email attachment and targeting companies using phishing attacks, it first attempts to connect to a command and control server, after connecting it generates a 2048 bit public and private key pair and uploads the private key to the command and control server. The ransomware then begins to encrypt the data on any local or network storage drive that it can gain access to. The public key that was generated is stored on the computer and the private key is stored on the command and control server. This is known as asymmetric encryption, the public key encrypts your data and the private key is used for decryption. This is the same way secure websites work, where the public key is given to your web browser and the private key is stored on the web server.
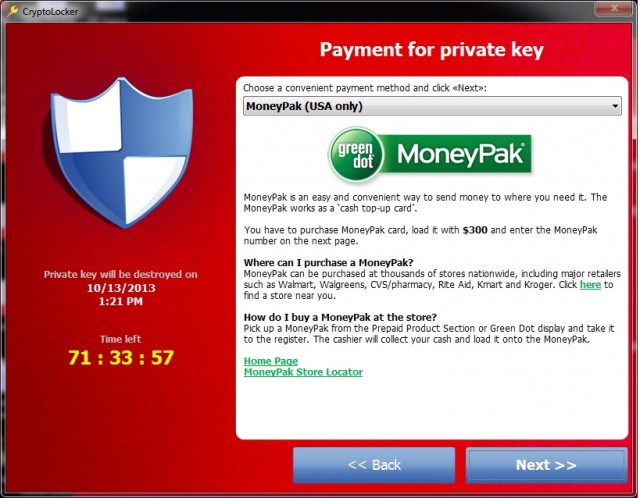
Cryptolocker demands payment to recover the key and threatens to delete the private key if payment is not received within 3 days. Although in a recent change of tactic now the infected users are having to pay $300 up front to receive the private key, but are also being offered a late payment option of $2000, and in an almost stranger twist Cryptolocker has setup a website where you can pay with 10 Bitcoins for decryption keys. At the current going rate 10 Bitcoins is roughly $2,200 USD.
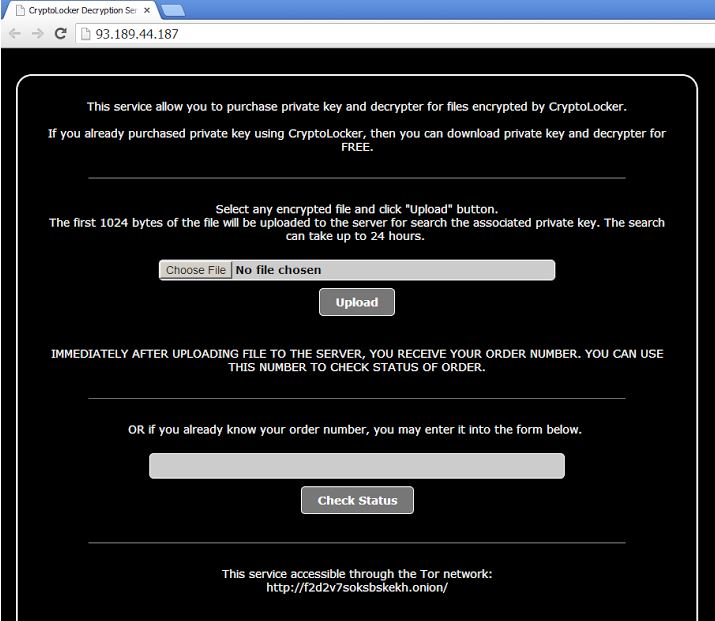
The Cryptolocker decryption service is available at yocmvpiarwmfgfy.net registered in Italy in September, http://93.189.11.187 a Russian based hosting server, or through the Tor network http://f2d2v7soksbskekh.onion. For those unfamiliar with the Tor network, “Anonymity Online” “Protect your privacy. Defend yourself against network surveillance and traffic analysis.” is their tag line. There are a lot of very good, legitimate reasons to use the Tor network, this is not one of them.
The Cryptolocker infection has been seen in Europe, the Middle East, North America and Asia Pacific with 64% of the victims being in the US.
So what do you do if you’ve been infected by Cryptolocker or other Ransomware? Likely you yell or cry, after that you have a couple of options. Having an attached external hard drive won’t help you, neither will having a backup service like Carbonite. The reason being with an attached external hard drive, it’s attached and all those files will also have been encrypted. The reason Carbonite won’t help is that as file updates are noted, including the change from an unencrypted file to an encrypted file that new file is now uploaded and has taken the place of of your previous version. If your business is running a true Enterprise Online Backup, which we highly recommend, you will have had the option to store multiple versions of your files, so while the newly encrypted file was uploaded on Thursday, the version from Monday is safe and sound waiting to be retrieved.
If you are in the position of having an enterprise backup solution like this, you will not be stuck paying the ransom, you will instead be able to wipe and reload the computer or server, reload your software and recover your unencrypted files from the enterprise backup.
If this is not the case you’re stuck with the painful question of how important are those files, do you need them badly enough to pay the ransom or can you live without them and move forward with a simple wipe and reload?
[whohit]CryptoLocker[/whohit]



5 Comments
Saved as a favorite, I love your website!
There is certainly a lot to know about this topic.
I like all of the points you made.
Excellent post. Keep posting such kind of info on your blog.
Im really impressed by your blog.
Hi there, You’ve done a fantastic job. I’ll certainly digg it and in my opinion suggest to my friends.
I am sure they’ll be benefited from this website.
You can definitely see your enthusiasm within the work you write.
The sector hopes for even more passionate writers such
as you who are not afraid to mention how they believe. At all
times go after your heart.
Good day! I just would like to offer you a big thumbs up for
the great info you have here on this post. I’ll be returning to your website for more soon.